“The motivation of the malicious actors is irrelevant; if an organization’s exposed sensitive systems are exposed to the internet with no security hardening, they are
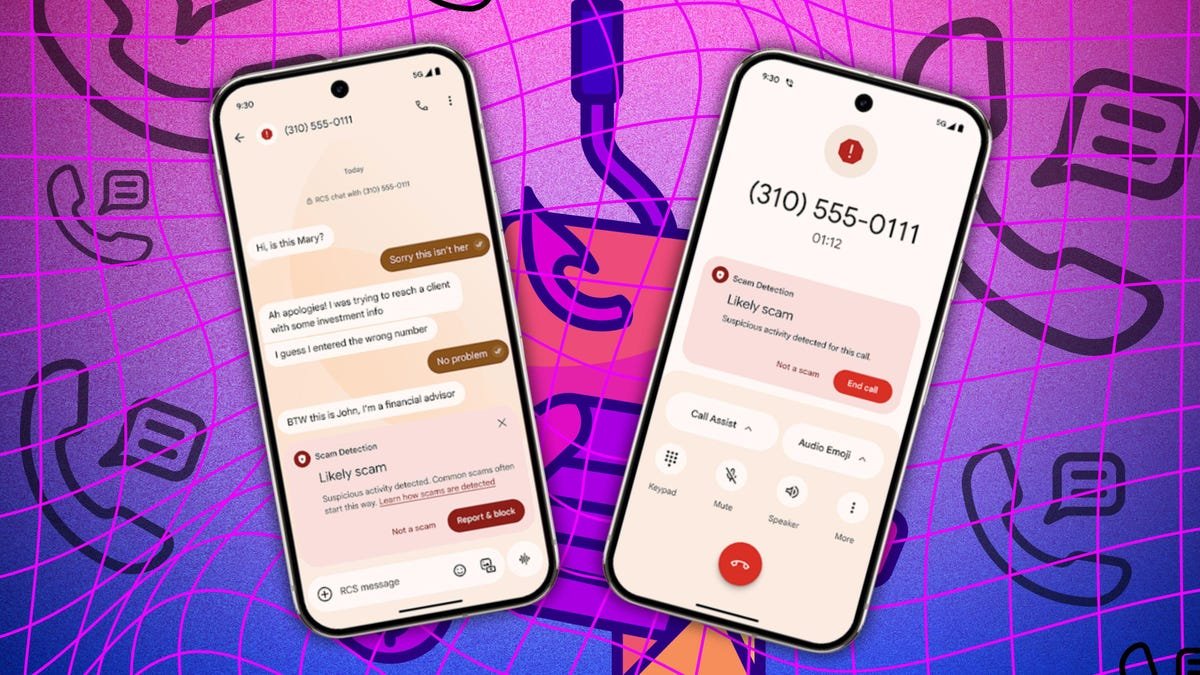
ZDNET Scammers are always looking to exploit the tools and technologies we use to steal our personal information, money, or both. That’s why companies like

Cisco has fixed a maximum severity flaw in IOS XE Software for Wireless LAN Controllers by a hard-coded JSON Web Token (JWT) that allows an unauthenticated

Once a threat actor is on an endpoint, EDR solutions are often the only obstacle between them and their objective – whether that’s deploying ransomware,

Table of Contents Close Table of Contents Key Takeaways: Where to Watch Ligue 1 Sign up for NordVPN at a 72% discount. There’s a 30-day

Security giant CrowdStrike has revealed it will lay off 500 workers as part of “strategic plans” to reach $10 billion in annual recurring revenue (ARR)

A new malware called LOSTKEYS, capable of stealing files and system data, has been identified by Google’s Threat Intelligence Group (GTIG) as part of a series

Since 2020, there has been a sharp rise in the number of cyberattacks targeting educational institutions. And PDF malware is one of the most common

May 08, 2025Ravie LakshmananThreat Intelligence / Ransomware Threat actors with ties to the Qilin ransomware family have leveraged malware known as SmokeLoader along with a

Cyberkriminelle haben Zehntausende Menschen in Deutschland mit gefälschten DHL-Nachrichten getäuscht. nikkimeel – shutterstock.com Laut einer Recherche des Bayerischen Rundfunks (BR) hat eine internationale Betrügerbande Zehntausende






