The ZBook line of portable workstations offers plenty more juice than conventional slimline ultraportables – largely thanks to higher-powered components and a dedicated graphics card.

Edge devices have become prime targets for cyber threat actors, particularly routers that are no longer receiving security updates and patches, leaving them vulnerable to

Pylarinos added: “There are several proactive steps that security teams can also take to mitigate vulnerabilities. If this news shows us anything, it’s the insecurity
hh5800/Getty Images Do you sometimes feel stuck in a Catch-22 regarding your long-term credential management strategy? You are. On the one hand, if the tech

Since the start of the year, the Russian state-backed ColdRiver hacking group has been using new LostKeys malware to steal files in espionage attacks targeting

The NCSC’s new Software Security Code of Practice is a “clear call to developers” to beef up secure by design practices, according to a senior

A wave of cyber incidents affecting operational technology (OT) and industrial control systems (ICS) in US critical infrastructure sectors has prompted a renewed call for
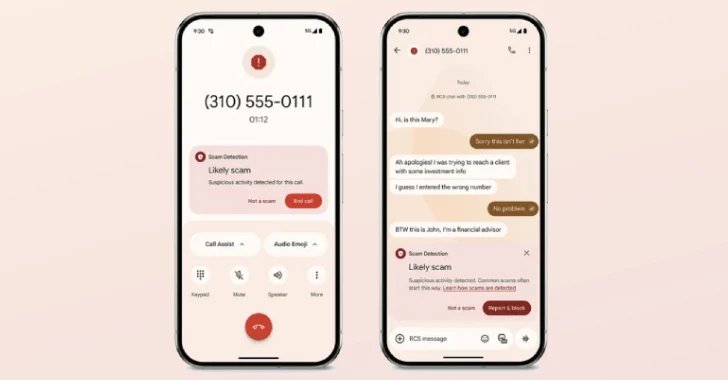
May 09, 2025Ravie LakshmananArtificial Intelligence / Online Fraud Google on Thursday announced it’s rolling out new artificial intelligence (AI)-powered countermeasures to combat scams across Chrome,

What distinguishes CTEM from other methods? CTEM differs fundamentally from conventional security methods because risks are recognized and assessed more quickly. Traditionally, many organizations rely

Venture capital firm Insight Partners has confirmed that sensitive data for employees and limited partners was stolen in a January 2025 cyberattack. Insight Partners is






